 4.9 out of 5 based on 4000 Students Rating
4.9 out of 5 based on 4000 Students Rating

The demand and popularity of cyber security course in delhi are increasing rapidly due to the advancement in technology and the use of the internet. Cybersecurity is the practice of protecting computers, mobile devices, and data from malicious attacks or several types of data breaches. It is often known by the name of information security(INFOSEC) or information Assurance(IA), System Security. Reports state that the first cyberattack occurred in France in 1834 when the two thieves stole the financial market information by hacking a French Telegraph System. These two thieves were responsible for disrupting the phone services and wireless telegraphy and the same but more devastating increases over time. The increasing activities of cybercrime have developed concern for data security. To deal effectively with malicious attacks, it require a cybersecurity professional. There are lots of cyber security institute in India offering effective cyber security training in India, ensuring a safe and protective system. As of now, cyber security course in India are gaining enormous popularity because of the increasing demand for cybersecurity professionals.
The evolution of cyber security holds a very fascinating journey that shows the rapid evolution of technology. The evolution of cyber security came to light in the 1970s because of the development of viruses and the same with the cyber security course in India. Internet data also claims that Bob Thomas created a computer program called “Creeper” in the 1970s that crawls the ARPANET network, leaving a breadcrumb trial. The story of cyber security begins with the birth of the first computer virus in the 1970s with the growth of sophisticated cyber threats, leading to major data breaches. This has offered the development of advanced cybersecurity technologies and also the growth of cyber security institute in India. The evolution of cyber security starts with a critical understanding of the digital threats.
Addressing the current scenario, the more connected we are, the more important cybersecurity. It is all about protecting people as well as their networks from several vulnerabilities. However, these days, emotional killing and social engineering networks are the powerful tools used by hackers to gain unauthorized access and play with the information. At the same time protecting them is never higher for the cybersecurity professionals. Cyber security course in India facilitates people gaining in-depth experience in tackling hackers and helping users to make their computers as safe as possible. Cyber Security Institute in India trains individuals to find and fix the vulnerabilities before they can be exploited.
So, to effectively tackle the complicated vulnerabilities, the cybersecurity professional must deepen their knowledge and understanding in the field of information technology for understanding the digital threats. They can also join cyber security course in India for a comprehensive overview of digital threats and ways to mitigate them.
Cyber Security is all about protecting and recovering computer systems, networks, devices, and programs from cyber attacks or by hackers. The practice of cybersecurity is used to protect companies and business data from phishing schemes, ransomware attacks, data breaches, and financial loss.
The recent era has gone through advancements in technology and life gets more dependent on technology as we are getting more connected to the internet. The benefits of the cyber security trends start from instant access to information on the internet, accessing smart home automation technology and concepts like IoT.
Every good thing comes from technology and it is very hard to believe that it can also lead to major cyber threats presented by the modern world. As per the information, the world has seen a sudden rise in cybercrime highlighting the importance of cybersecurity today and also the demand for cyber security course in India. The scenario of increasing cyber security threats has created concern for cyber security institute in India. Now, it is very necessary to capture the true nature of cybersecurity to identify the theft and let them not use digital weapons. So, for those cyber security training in India is designed to understand the complexities of cyber security and make it accessible for everyone.
As a matter of fact, the modern world is dependent on technology, and as this dependence grows over time, so will the likelihood of digital threats. Cybersecurity is more effective here. This field focuses on safeguarding against all types of cybercrime, including digital weaponry and identity theft. Despite being one of the finest defenses against data breaches, it can be pointless if one is unaware of the intricacies of cybersecurity.The work of a strong cybersecurity policy is to secure computer systems and networks from unauthorised access to survive in today’s competitive world. Furthermore, competing with the hacker requires the right tools and cyber security strategy which can be learned by joining the cyber security course in India. There are lots of cyber security institute in India that works together to serve individuals with the right approach of cyber security.
Cybersecurity is becoming more and more significant in today's environment. Protecting client data through the use of cloud security solutions and strong password policies is the top priority for cybersecurity. These days, people keep sensitive data online or on cloud storage platforms like Dropbox or Google Drive, including social security numbers, credit card numbers, and bank account information. This increases the risk of data breaches that result in loss of information and money. Therefore, cybersecurity's engagement is crucial to reducing the rapid rise in cyber risks. A person can swiftly review data breaches and communicate with all data breaches and potential risks by enrolling in an cyber security institute in india.
In-depth instruction in protecting a person's system and network is provided by GICSEH, which offers cyber security course in India. In order to protect customers from different types of cyberattacks, such as DDoS and phishing, cyber security institute in India exchange information and experience about cyberattacks and cyberdefense.
Consider an image of a worker or person interacting with data from the rear. A hacker tries to surreptitiously obtain unauthorized access to private data, obtains all of the sensitive data, and then sells it to criminals. For the sensitive data to be returned, a hacker may demand a ransom.
You might imagine how catastrophic that will be, but fortunately, all data is housed online these days, and data breaches are now commonplace. However, safeguarding a company's sensitive data is an essential component of corporate strategy, which has raised demand for cyber security course in India.
In today world, the demand for cyber security course in india is constantly increasing. It is a practice of securing the computer network, systems, information, and practice to make the hackers aware of the modification or unauthorised access. There are different types of cyber security practices including network security, application security, data security, and operational security to protect resources and online information from breaches.Cyber Security Institute in India teaches individuals about cyber security and how cyber security works. Getting cyber security training in India upskills the individual to build a career in cyber security and makes them aware of the complexities of keeping the threats away from the computer network.
According to the information, an average of 130 cyberattacks an organization experiences every year. Data breaches have become a common occurrence and security breaches grew by 27.4% in 2020. The impressions of cybercriminals are increasing and creating a concern for the organisation and business owners.
This creates the importance of cyber security and the demand for cyber security course in India. Companies or organisations need cyber security professionals to protect the security and integrity of networks. Joining a cyber security Institute in India offers various training to safeguard the sensitive information.

1. Helps in Protecting Sensitive Information
The primary purpose of the cyber security professional is to protect sensitive data such as personally identifiable information or business data.The purpose of cyber security is to prevent unauthorised access by implementing security controls, access controls, and data breaches.
2. Defend Cyber Threats
The complexities of cyber threats becoming more advanced and mitigating the potential of cyber attacks requires a knowledgeable cyber security expert. Cyber security professionals are trained to quickly find the threats and malware attacks and respond to them to break their chain attacks. To defend the cyber threats effectively cyber security institute in India is offering detailed knowledge on maintaining the security of computer networks. Cyber security course In India helps individuals to analyse security risks and implement security controls accordingly.
3. Enhance Network Security
Deploying strong security measures is the key thing to maintain the security of computer networks. Cyber security professionals focus on adding extra layers of security such as firewalls and intrusion detection systems to prevent unauthorised access. However, the process involves various tools and technology to inspect the unknown threats and take protective measures. To get information about enhancing network security, a cyber security course in India is best suited.
Cyber threats and cyber attacks refer to malicious activities that seek to damage, steal, and disrupt the digital life of an individual. There are different types of cyber threats and attacks to steal the personal information of the users. It includes sending computer viruses, data breaches, Denial of service(DoS) attacks, and various other attacks. Sometimes cyber attacks are also referred to as getting unauthorised access to the information and further use for malicious activities or damage and disrupt the personal information. The information of the individual can be in any form like the technology asset, computer network, intellectual property, or any form of sensitive data. Sometimes, the cyber threats may also come from within the organisation by trusted users or from unknown parties.
In the era of fastest growing internet, it would not be wrong to say that cyber threats affect every aspect of life like electrical blackouts, military equipment failure, breaches of national security secrets, and much more. Cyber threats as well as cyber attacks have the potential to disrupt computer networks and phone networks while making the data accessible and vulnerable. Right now, cyber threat management is rolling to protect the information and secrets of individuals and address the overall cybersecurity needs of today. Furthermore, this has also created a demand for cyber security course in India. There are various cyber security institute in India delivering the hands-on experience of cyber security to effectively deal with the complexities of the rising cyber threats.
Cyber threats and attacks are often referred to as malicious activities intended to steal and damage the information and sensitive data of an enterprise. It can disrupt digital stability which includes a wide range of digital threats including data breaches computer viruses, denial of service, and various other attacks. Another definition of the cyber threat is, anything which is intended for the potential disaster of digital information or digital assets is known by the name of cyber threats.
Cyber threats potentially attack computer systems and networks and cause everything from Trojan viruses to hackers and back doors. In most cases, cyber threats involve multiple exploits of information and disrupt digital life in general. So, to mitigate the potential exploitation of the information cyber security training in India is offering a well-developed yet effective training program to be aware of the rising complexity of the cyber threats and then the potential steps to remove the hands of hackers from the sensitive data.
As discussed above there are various types of cyber attacks and threats and each one comes with its own set of techniques and objectives. Some of them are highlighted below.
A malware attack is a disaster program designed and intended to compromise data confidentiality, integrity, and availability. It is a set of programs inserted by hackers in app downloads, mobile websites, phishing emails, and text messages. Once, the device has been compromised, the hacker can easily get access to personal information, location, financial information, and much more. There are various types of malware attacks among them some of the most common types are:
1. Virus: This is one of the most common types of malware attacks to steal the personal information and sensitive data of the individual. Generally, viruses are spread throughout the computer network attached to a file which can corrupt or delete the data device.
2. Trojans: Trojans are far different from the viruses which are meant for the more destructive as the trojans enter the system looking like legitimate software but act as malicious ones.
3. Worm: It is also a type of malware attack that enters locally in the computer network or through the internet. After entering the computer network it starts exploiting the vulnerabilities in the operating system.
4. Spyware: As the name indicates Spyware, usually this type of malware long spies on the user's operating system. These types of attacks gather the user's data and sensitive information like user habits, logins, credit card information, and other personal details. The malware hides their identity on a device and provides real-time information like bank details and passwords.
5. Rootkit: This type of malware is designed to gain access to a device. These types of malware come with more complexity and deeply embedded in the device and are difficult to detect.
It is one of the most dangerous hacking techniques used by the cybercriminals to exploit the vulnerabilities. It largely relies on human error rather than technical vulnerabilities. It provides sensitive information by installing malware on the device acting as a legitimate actor. Common types of social engineering attacks are highlighted below.
1.Phishing: The technique of phishing attacks uses the email address to catch the recipient and disclose their confidential information. A user can download the malware into their computer system by just clicking on the hyperlink in the message.
2.Smishing(SMS Phishing): In SMS phishing, the attackers use text messages with malware to steal the user's identity.
3.Baiting: This is also called a social engineering trap and usually promises something more attractive like a gift card to get the victim's sensitive information such as bank details and other credentials.
The supply chain attacks aim to infect the authentic application and spread malware through the source code, build processes, or software update mechanisms. In these attacks, a hacker tries to find insecure network protocols, server infrastructure, and coding techniques to steal the privacy of the users and compromise with the sensitive information. An attacker can also modify the source code and hide the content making it difficult to detect for the cybersecurity professionals. So, to cater the Cybersecurity industry, there are numerous cyber security course in India intended to build a solid foundation of cybersecurity concepts.
As the name indicates injection, it injects malicious software into the web application code and may expose sensitive information. It may compromise the entire system and may lead to further vulnerabilities. Some of the injection attacks include SQL Injection, Code injection, cross-site scripting, etc.

The digital age has brought to humanity ease and connectivity like never before, but it also comes with the associated rising cyber threats. From data breaches to ransomware attacks, the face of cybercrime is getting more and more sophisticated every day. From within this complex and dynamic environment, ethical hacking has emerged as a very integral component of robust cyber security course in India.
Ethical hacking, also known as "white hat hacking," refers to the use of hacking techniques for any authorized purposes. Such are the ethical hackers, popularly referred to as white hat hackers, who search out weakness or vulnerability in systems, networks, and applications to expose
any lurking threats in the system and hence try to mend the loop holes so that negative hackers do not exploit those loopholes. In contrast to black-hat hackers, ethical hackers always have explicit permission, and there exist rigorous ethical guidelines to keep their activities in check.
Proactive risk assessment: Ethical hackers dive deep into identifying weaknesses in an organization’s security infrastructure. Simulating real-world attacks helps uncover vulnerabilities that cybercriminals might exploit. For those seeking to enhance their skills in this area, pursuing a cyber security course in India or an Ethical Hacking Course in India can provide hands-on experience and insights into ethical hacking techniques.
Vulnerability discovery and remediation:A critical role of ethical hackers is identifying vulnerabilities and providing timely reports to organizations. This allows for quick remediation, reducing the likelihood of successful cyber-attacks. Top cyber security institute in India offer in-depth training in vulnerability assessment and ethical hacking.
Improved security posture: By understanding the tactics used by malicious hackers, ethical hackers can help organizations implement robust security measures, conduct regular security audits, and educate employees on cyber threats. Enrolling in cyber security training in India ensures professionals are equipped to tackle such challenges effectively.
Compliance and Risk Management: compliance adherence is expected by organizations from the contemporary regulatory landscape. Penetration testing will show an organization's compliance in the best way by picking out potential flaws that may be abused to gain unauthorized access.
An ethical hacker has a wide array of skills that will enable them to effectively do the job. Some of these include:
1.Network Security: The ethical hacker studies the network protocols, vulnerabilities, and penetration testing techniques.
2.Application Security: Testing software applications for inherent weaknesses; secure coding practices are developed.
3.System Hacking: In-depth knowledge of operating systems and system vulnerabilitie.
4.Cryptography: Studying the encryption algorithms and how to apply them in practice to secure data.
5.Social Engineering: It involves the underlying human psychology that could be applied to identify possible social engineering attacks.
To develop these critical skills, aspiring ethical hackers can enroll in specialized cyber security course in India offered by leading cyber security institute in India. These programs provide comprehensive training to build a strong foundation in ethical hacking and cybersecurity.
Cybersecurity has become a crucial part of any business in the digital age we live in today. In the rising frequency and complexity of the attacks, the protection of sensitive data and systems has ceased to be an option but rather a necessity in today's competitive marketplace. Effective implementation of these practices protects your business from potential threats.
Cybercriminals continually become better at the tactics of revealing their vulnerabilities. Those who are exposed can bring about devastating scenarios for businesses if a breach involves a ransomware attack or data loss. You can avoid, as a business, what you are aware of as the most recent threats.
An effective cyber security strategy clearly defines how the organization will manage and mitigate potential cyber risks and is the cornerstone of a well-protected business landscape.The components of a comprehensive one would include the following:
Risk assessment:
Policy documents Employee training Incident response planning Technology implementation
Essential Best Practices in Cyber Security Employee Awareness and Training
An organization's employee is always the weakest link in any security chain. In fact, cyber security training in India ensures that at least people can get a hands-on idea of how to identify and react to potential threats. Regular cyber training sessions need to be in place, covering topics like phishing scams, social engineering, password hygiene, and data handling practices. Fostering a culture of security awareness often goes a long way toward minimizing errors on the human front.
It is at the core of safeguarding all that your systems hold, and there are several ways to come by it. First, encourage employees to develop strong passwords featuring upper and lower cases, numbers, and special characters. Additionally, consider implementing multi-factor authentication (MFA) for added security. Establish good password policies.
It is important to keep software and operating systems up-to-date to help patch vulnerabilities that cybercriminals can otherwise exploit. Turn on automatic updates wherever possible. Keep checking and installing critical updates at regular intervals to ensure that your systems are safe from potential risks.
Data Encryption:
Data encryption is a strong mechanism to protect information. To avoid exposure to unauthorised people, encrypt the data both at rest and in transit. This is especially important for information stored in the cloud or transferred across networks. A good network security infrastructure is what safeguards a business from any kind of external threat. It is important to install firewalls, intrusion detection and prevention systems (IDPS), and network segmentation for continuous layered protection. It is good practice to monitor and analyze network traffic at regular intervals to find and eliminate any potential vulnerabilities. Data encryption makes sure that only the right people should have access to sensitive information and systems. You constantly need to review and update these access privileges, making sure the new needs always take precedence.
Regular Security Audits and Assessments:
Periodic security audits and evaluations are required to fix the existing vulnerabilities and discover new ones. Identify weaknesses to avoid and manage, and have the assessment targets regularly for effective remediation efforts. Regular security audits and system assessments can help you point out the vulnerabilities and weaknesses of the system from time to time. It can help you to highlight the potential threats before happening. Consider hiring an expert in cybersecurity to do the evaluations.
Backup and Disaster Recovery:
Back up your data regularly. This backup strategy must be a good one that allows on-site and off-site backups of data. You should test your backup procedures frequently to verify data restoration if a disaster were to happen.
Modern society offers dangerous opportunities for cyber threats at both the individual and organizational levels. The impacts of cyber attacks can vary from financial losses to reputational damage. Technology, however, has been at the core of defence human error, on the other hand, has come out to be one of the major weaknesses. Thus, cyber security training in India is quite important in bridging this gap. Employees can be empowered with knowledge for the identification of risks and how to react to them, hence building a stronger security posture.
Evolving Threatscape
The threat landscape today is a complex and dynamic one due to the rapid advancement in technology. Cybercriminals get more sophisticated. They are highly innovative when it comes to exploiting vulnerabilities. Examples include phishing, ransomware, and social engineering. Be proactive against such adversaries.
It is said that employees are the weakest link in the security chain well, that is quite a half-truth. On the one hand, human error can certainly be what leads to breaches on the other, it could be the first line of defense. Cyber security training in India turns your workforce into an asset by making them vigilant and knowledgeable.
Benefits of Cyber Security Awareness Training
1.Reduced Risk of Cyberattacks: Organizations can substantially bring down the chances of successful attacks through employee education on common threats, including phishing and social engineering.
2.Improved Incident Response: Employees who are properly trained are much faster at identifying and reporting doubtful activities. Therefore, they enable the organization to respond to any incident at the right time.
3.Enhanced Data Protection: Such awareness training programs build a robust security culture that would provide the required impetus for the protection of sensitive information against unauthorized access and any form of misuse.
4.Cost Reduction: Cyber attacks may be very expensive in terms of loss of money and reputation. If an attack can be prevented, the organization saves huge costs.
5.Compliance Maintenance: Several sectors have severe data protection policies. Cyber security awareness training will support such organizations to adhere to compliance requirements and avoid large penalties.
A successful cyber security awareness campaign should contain the following elements:
1. Cyber Threat Awareness: Educate employees on the various types of cyber threats, including phishing, ransomware, malware, and social engineering.
Password Management: Educate workers on the importance of strong, unique passwords, and the perils of sharing them.
2. Data Protection: Educate on the importance of data and ways in which one can secure sensitive information.
3. Incident Reporting: Develop and communicate procedures on how to report any suspicious activity; ensure there is open communication from all levels of employees.

4. Mobile Security: Highlight the risks associated with using mobile devices for any work-related activities.
5. Social Media Security: Educate employees regarding the dangers of using social media and how they can contribute to safeguarding personal and professional information.
Setting up an effective cyber security awareness program may not always be easy. Some common challenges include:
Resistance from Employees: A few employees view security training as a painful disturbance or a time-consuming activity.
Lack of Management Support: It may be challenging to get hold of resources and time with no executive buy-in on training.
Keeping Abreast: An evolving threat landscape makes it hard to keep training materials up to date. The ability of organizations to overcome these challenges calls for the need to make training both engaging and relevant and to involve management in the process. This calls for continuous investment in training and education.
Measuring Impact: Any cyber security awareness program must be measured by the organization for effectiveness on key metrics: the number of clicked phishing attempts, the number of security incidents reported, and the satisfaction of employees with the training.
While this is so, it often benefits from supplementation with external expertise. Depth cyber security training in India is available through the likes of the GICSEH. Such knowledge and practical skills will hence be very vital for the person so that they will be able to keep up with changing cyber security. One critical component of an all-inclusive security strategy in the organization has to be cyber security awareness training. The more educated and empowered an employee, the less likely he will be to allow access to an attack.
GICSEH Cyber Security Course in India, to empower students and working-class people with skills and knowledge to make a difference in this most important area. Through this Cyber Security Institute in India, you too can be an expert in saving your organization from increasingly growing cyber threats.
The age of the digital revolution brought to the world a moment where information has become more priceless than ever. With the ever-increasing dependency on technology, the level and complexity of cyber threats are increasing more devastatingly. Cyber-attacks are sophisticated, targeting individuals, business enterprises, and governments without any discrimination. This has raised the demand for professionally skilled cybersecurity experts. A Cyber Security Course in India has emerged as a highly sought-after qualification, and obtaining a cybersecurity certificate is fast becoming the most important step towards a successful career within this field.
The Growing Importance of Cybersecurity
The increasing frequency and severity of cyberattacks have brought cybersecurity to the top of the agenda for many organizations across the globe. Data breaches, ransomware, and identity theft, among other espionage activities, can cause potential disasters in case of any cyber incident. Businesses are, therefore, making heavy investments in their cybersecurity defences, giving rise to a boom in the job market for such experts.
A Cyber Security Institute in India offers elucidating course programs, exhibiting the effective usage of safeguarding digital assets. The program includes subjects on network security, cryptography, incident response, and digital forensic analysis. After completing a cyber security course in India, one will have a better standing to be in a position to understand the waves of threats and vulnerabilities to come up with a measure against the same.
The cybersecurity method deploys a series of technologies, processes, and various methods to defend computer system data, and networks from attacks. It protects and defends internet-connected devices and services from malicious attacks by hackers, spammers, and cybercriminals. Most companies as well as firms use cybersecurity practices to protect their information against phishing schemes, ransomware attacks, identity theft, data breaches, and financial loss. Looking around today’s world, our daily life is dependent heavily on technology than ever before. The benefit is the instant access to information through the Internet making it a way of modern convenience bringing together the concept of smart home automation and the Internet of Things. With so much advancement in technology, it is very hard to believe that potential threats lie behind every device and platform conveying modern technology a real danger. These concerns force us to learn more about cybersecurity including cyber security threats. The best answer to the question “How does cyber security work” hides in a series of subdomains like application security, cloud security, identity management and data security, mobile security, network security, and much more. So, to protect the organisational assets from a wide range of cyber threats it is necessary to enroll in a cyber security training in India.
1.Application Security
Application security is a major contribution to implementing different sets of defences within or outside the organisations. It provides a range of software and services to protect against cyber threats. The subdomains of cybersecurity require a cyber security expert to write a series of codes intended to secure application architecture, implement robust data input validation, and more to mitigate the chances of getting unauthorised access or modification of data.
2. Cloud Security
The cloud security subdomain is used to secure cloud architectures and applications for the big companies and firms that use cloud service providers like Amazon Web Services, Google, Azure, Rackspace, etc. It implements a powerful security system framework to manage huge data. Cyber security Institute in India teaches the best practices to implement effective security systems.
3. Identity Management and Data Security
The identity management and data security subdomains include activities like frameworks and processes that facilitate the users with the authorisation and authentication of legitimate individuals. The whole process implements a powerful mechanism that secures useful information in both the server and the computer. Furthermore, the subdomains add extra security and authentication protocols by enabling two-factor or multi-factor authentication.
4. Mobile Security
Addressing the current scenario, people heavily rely on their mobile devices for a wide range of services. Today, mobile security is a big deal as mobile devices are the major source of data vulnerabilities. So, the subdomains of mobile security protect the organisational and personal information of the users stored on their mobile devices like tablets, and cell phones. Mobile security protects the device from getting unauthorised access, device loss or theft, malware, viruses, etc.Cyber security course in India shares all the related information about cybersecurity to deal with real-life challenges.
5. Network Security
Network security is a technique for practising, measuring, and using technologies to protect the computer network. It works well during data transmission due to various forms of security threats and unauthorised access. With the growing technology, the trend of data transmission became increasingly popular leading to network vulnerabilities. This is where the network security prevents the network from vulnerabilities, further protecting the data transmission. Network security is a process that involves implementing protection such as firewalls, intrusion detection systems, encryption, access controls, and regular monitoring of the network to detect future vulnerabilities. Furthermore, it helps to protect and mitigate cyber threats.
Cybersecurity and information security are closely related but dont hold the same meaning. Information security is intended to safeguard data from unauthorised access or manipulation while cybersecurity is a broader field that covers various aspects of security including protecting devices, networks, and systems from cyber threats. Cybersecurity goes beyond online data and attempts to preserve the entire digital ecosystem. However, both cybersecurity and information security are closely related and work together to protect and secure the digital infrastructure of an organization. Furthermore, cybersecurity and information security act as a shield to ensure extra security to the system.
The increasing frequency and severity of cyberattacks have brought cybersecurity to the top of the agenda for many organizations across the globe. Data breaches, ransomware, and identity theft, among other espionage activities, can cause potential disasters in case of any cyber incident. Businesses are, therefore, making heavy investments in their cybersecurity defences, giving rise to a boom in the job market for such experts.
A Cyber Security Institute in India offers elucidating course programs, exhibiting the effective usage of safeguarding digital assets. The program includes subjects on network security, cryptography, incident response, and digital forensic analysis. After completing a cyber security course in India, one will have a better standing to be in a position to understand the waves of threats and vulnerabilities to come up with a measure against the same.
How Does Cyber Security Work?
The cybersecurity method deploys a series of technologies, processes, and various methods to defend computer system data, and networks from attacks. It protects and defends internet-connected devices and services from malicious attacks by hackers, spammers, and cybercriminals. Most companies as well as firms use cybersecurity practices to protect their information against phishing schemes, ransomware attacks, identity theft, data breaches, and financial loss. Looking around todays world, our daily life is dependent heavily on technology than ever before. The benefit is the instant access to information through the Internet making it a way of modern convenience bringing together the concept of smart home automation and the Internet of Things. With so much advancement in technology, it is very hard to believe that potential threats lie behind every device and platform conveying modern technology a real danger. These concerns force us to learn more about cybersecurity including cyber security threats. The best answer to the question “How does cyber security work” hides in a series of subdomains like application security, cloud security, identity management and data security, mobile security, network security, and much more. So, to protect the organisational assets from a wide range of cyber threats it is necessary to enroll in a cyber security training in India.

These days, cyber security is a major concern for both individuals and companies. The significance of having the right tools and methods to handle sensitive data and systems should not be understated, especially as cyber threats are always changing. These can help one stay alert, whether they are taking a cyber security course in India or are extending their knowledge through real-world applications.
1. The First Line of Defense: Firewalls
A firewall is a type of access control that keeps untrusted external networks, such as the internet, apart from trusted internal networks. In accordance with pre-established security criteria, it monitors all incoming and outgoing communication and prevents unwanted access. Because they make sure that only genuine traffic passes through, firewalls are crucial for defending sensitive systems from malicious attacks. GICSEH, the best cyber security institute in India offers courses on firewall configuration and management.
2. Software for Antivirus and Anti-Malware
When it comes to identifying and eliminating harmful programs like viruses, worms, and spyware, antivirus software is essential. By identifying more complex threats, such as ransomware and zero-day exploits, anti-malware technologies go one step further. Deploying and updating these technologies requires this knowledge, which is why GICSEH Cyber security training in India offers thorough instruction.
3. Systems for detecting and preventing intrusions (IDPS)
A sophisticated instrument called an IDPS is made to keep an eye on network traffic for unusual activity and to automatically stop such attacks. An IDPS adds an extra degree of protection by examining data packets and spotting irregularities. You can get practical experience with a variety of IDPS solutions at GICSEH, which will help you effectively defend systems against changing cyberthreats.
4. Techniques for Data Encryption
Data can be secured by encryption, which turns it into an unintelligible code that can only be decrypted using a decryption key. It ensures that private information won't be exposed even if it is intercepted by cybercriminals. Modern encryption methods like AES and RSA are now often used to protect emails, personal information, and financial transactions. GICSEH's cyber security course in India offers in-depth understanding of how encryption is implemented on different platforms.
5. Tools for Penetration Testing
In order to find current vulnerabilities, penetration testing simulates carrying out cyberattacks on a system. Metasploit, Nessus, and Burp Suite are popular tools for this. Using penetration testing, one can get ready to examine security flaws before they allow attackers to gain access. GICSEH provides students and working professionals with specialized cyber security training in India so they may become proficient in it.
The growing demand for skilled professionals has led to the emergence of several cyber security institute in India. These institutes provide specialized training programs designed to equip individuals with the knowledge and skills needed to excel in this field. Students enrolling in a cyber security course in India are provided with a structured curriculum, experienced instructors, and hands-on training that prepares them for real-world challenges.
As India speeds ahead into digital transformation, cyber security is at the top of the national agenda. As one of the fastest digitalizing economies in the world, India has just as many cyber security threats, and enforcing good digital defences is now critical for everyone from individuals to businesses and governments. We will examine the recent trends and predictions for the future and how the landscape will change the future of cyber security in India.
Recent Trends Leaving their Mark in Cyber Security in India:
1. AI Impacts Both Ends of the Cyber Security Landscape
Artificial Intelligence (AI) and Machine Learning (ML) has made an impact on both of the angles of cyber security. Organizations have adopted AI and ML to boost their threat detection capabilities, automate their incident responses, and identify attacks before they happen. While cybercriminals are using AI to build better malware, phishing scams, and impersonation scams making it harder to differentiate between real and artificial interactions.
2. Centralisation of Cloud Services
Cloud Services have also become the central stage for organizations. With 62% of cyber detections happening in cloud services, the use of cloud services has influenced this advanced development. Many Indian organizations are migrating to cloud services for optimal performance purposes. However, services like support provider services and unsecured APIs have now become a target. Outcomes show securing cloud services is now just as important as securing sensitive traditional-based IT environments.
3. Ransomware-as-a-Service (RaaS) and Supply Chain Attacks
Ransomware remains a top threat you need to consider, but the way it's delivered has changed. The availability and proliferation of RaaS platforms are creating the opportunity for less-skilled threat actors to deploy attacks with more sophistication against targets in healthcare, finance, and government. Similarly, not only has the target range for attack expanded, but the frequency of attacks has too. There are way too many instances of attacks on software supply chains and critical infrastructure now targeting not only larger organizations but smaller partners that are more likely to lack sufficient cybersecurity.
4. Target Sector: Healthcare, Banking, and Hospitality
In 2024-2025, Healthcare became the most attacked sector (21.82% of all attacks), with Hospitality and Banking being next respectively. The criticality and the value of personal and financial information make these sectors prime for extortion, data breaches, and ransomware.
5. Issues Related to 5G, IoT, and Quantum Computing
India has begun rolling out 5G networks in 2024, alongside the sheer volume of IoT devices coming online, which will create a much greater attack landscape and threat surface. More endpoints = More cells/posts for attackers. In addition, the fact that quantum computing is real and will become mainstream in the next few years cannot be ignored - organizations will soon find themselves adding quantum resistant encryption as a part of their multi-layer defense.
6. Behavioral Threat Detection
Cyberstacks across India are beginning to change from being signature-based to behavior-based analytics which currently represents 14.5% of detections - up from 12.5%. Behavior-based analytics helps organizations identify new types of malware or evolved threats that signature-based detection failed to identify. Government and Regulatory Initiatives That the government of India has designated cybersecurity as a national priority, its agencies are the CERT-In (Indian Computer Emergency Readiness Team), I4C (Indian Cyber Crime Coordination Center), and the DPDPA (Digital Personal Data Protection Act) recently enacted. Some of the primary policies and initiatives are:
National Cyber Security Policy: Outlines policy and strategy developments to secure the digital infrastructure and increasing resilience.
Cyber Surakshit Bharat & Cyber Swacchita Kendra: Offering training and awareness of malware.
Mandatory Reporting Protocols: Mandatory reporting protocols, especially in finance and health, have improved measures to promote and act on cyber incidents and improve resilience within the sector.
Future Directions and Opportunities Market Size-The cybersecurity market in India was valued at 1.97 Billion USD in 2020; projected to grow to 3.05 Billion USD by 2025, which is nearly a 15.6% compound annual growth rate (CAGR).The growth of the market is propelled by the increase in threats, but also by digital transformation.
Talent/Workforce Demand: India is projected to have a shortage of skilled professionals, coupled with the demand for young and skilled professional cybersecurity workers, results in high-paying, future proof careers.
Collaboration and capacity building: The future requires increased collaboration between government and industry and international partners. Capacity building programs must be scaled, and laws must continuously evolve to counter emerging threats.
Emerging technologies: Areas of focus on will be AI threat intelligence, zero trust frameworks, deepfake detection, and blockchain for institutional data integrity.
Challenges to address
India continues to face an evolving set of challenges; outdated laws, no comprehensive cyber strategy, and limited skilled human resources are all elements that impact the speed of incident response and innovation. Surpassing highly sophisticated perpetrators of crime will require universal education to be aware of possible cyberattacks, continued R&D investment, and a shift to security by design.
The Cyber Security Skill Gap in India India is certainly experiencing rapid transformation and growth in the digital space, however, it has exposed a stark reality of a serious shortage of skilled cybersecurity professionals. The cybersecurity skills gap puts national security at risk, particularly with respect to businesses, the recent increase in attacks against critical infrastructure as well, and if finance is considered, even rapid GDP growth. Presented below is a full picture of the current landscape and the general perceptions including ongoing activity to remediate the skills gap in cybersecurity.
Extent of skills shortage
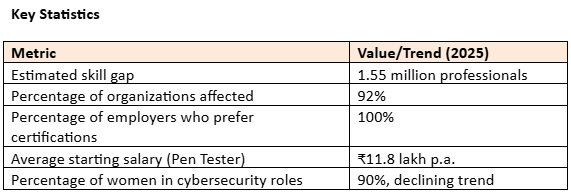
India requires over 1.5 million cyber security professionals just to meet its demands, with the skills gap also growing, meaning there are vacancies number of personnel shortages at all levels of the process, including roles in small, medium and enterprise companies.
By mid-2025, the country revealed a gap of approximately 800,000 jobs—one-fifth of the deficiency in the common manpower requirement for the global cybersecurity workforce.
There are only about 0.3 million cybersecurity professionals in force, unqualified for the jobs necessary to protect companies and public infrastructure from breaches--in short.
The main factors causing the gap are:
The rate of digitalisation. Initiatives like Digital India, Fintech and other platforms, cloud computing and the IoT have virtually increased the country's cyberattack surface area faster than we can train talent to assist in closing the gaps.
The academic training does not align with the asset readiness - most tradition IT courses still think of cybersecurity as a small module or elective, often failing to stimulate real-life, practical experience, and obsolete by the time it's completed or even the emerging future threats.
The ability of the workforce has become somewhat irrelevant because many of them lack the technical skills required by the industry.
Skill fatigue and turnover because of the rapidly evolving threat landscape often creates the stress of burnout, as organizations, already short-staffed, cannot retain staff. Cybercrime has become increasingly advanced and incident response management has not improved, or properly resourced.
Gender and Diversity gaps: There has been continued progress in the number and fraction of the women in cybersecurity workforce, however there has been an overall decline in women in the context of long-established diversity goals indicating the barriers of participation are still existing. Impact on Business & the Economy
The Cyber Security Skill Gap in India
India is certainly experiencing rapid transformation and growth in the digital space, however, it has exposed a stark reality of a serious shortage of skilled cybersecurity professionals. The cybersecurity skills gap has implications for national security in areas such as businesses, the recent spikes of attacks on critical infrastructure, and may also extenuate the rapid increase in GDP. Below is a full overview of the current state of play and contributing factors including ongoing initiatives to address the cybersecurity skills gap.
Security Breaches: 92% of organizational respondents reported security breaches as a result of cybersecurity talent shortages, which come with significant financial and reputational impacts; the share of organizations that report losing more than USD 1 million in an attack are seemingly increasing at an alarming rate.

Boardroom Issue: Cybersecurity is forefront of concern in nearly all major Indian organizations, and when organizations retain less talent, they pay even more for training, technology, and automation.
Increased accountability: There is a talent shortage, and as a result, the board is more attentive and executives are let go and fined with regard to failure. Closing the Gap: Trends and Tactics Training & Certification: 100% of organization respondents want their candidates to have recognized industry certifications (i.e. CEH, CISSP, CISM). 92% of organizations will spend money on their employees to gain certification to build a current-skilled workforce.
Reskilling and Next-Gen Technologies: Organizations will leverage automation, artificial intelligence enabled solutions, and continuous upskilling, to retain the challenges of security today.
Collaboration across the Public, Private Sector: Edtech companies, government programs, and industry organizations are working together to scale cyber education and provide hands-on training pipelines, including partnerships with CERT-In and various academic institutions.
Proactive Awareness: Cyber awareness programming for anyone, not just staff in IT roles, is seen as essential and companies are working to invest in simulated attack drills and real world exercises.
Demand and Careers Cybersecurity positions have high starting salaries, rapid advancement, and increasing opportunities in sectors such as healthcare, finance, e-commerce, and government. Cybersecurity skills gap in India presents challenges, yet presents an opportunity. Expanding training, more hands-on courses, advancing diversity, and linking to emerging technologies will help shorten the workforce gap, and put India on top of defending its expanding digital infrastructure.
Leading job posting regions (number of job postings) include Bengaluru, while all metros and remote work positions have additional potential for new growth.
The Way Forward
Cybersecurity skills gap in India presents challenges, yet presents an opportunity. Expanding training, more hands-on courses, advancing diversity, and linking to emerging technologies will help shorten the workforce gap, and put India on top of defending its expanding digital infrastructure. The Future of Cybersecurity in India
With India moving rapidly into the digital era, cybersecurity is a national priority. With one of the fastest-growing digital economies, now is the time for protecting national assets, as there is a rapid upward trend in cyber threats—therefore, ensuring organizations, governments, and citizens are practicing good, robust digital defence is a priority to stay ahead of the cyber threat game. Let’s look back at some trends, forecast for the future, and the ever-changing face of cybersecurity in India.
1. Artificial Intelligence Audits and Facilitates Defence and Attack
Artificial intelligence (AI) and machine learning (ML) have shifted the cybersecurity picture. Organizations are utilizing AI for efficient threat detection, automating incident responses, and anticipating attack. Cybercriminals use AI to develop sophistication malware, phishing campaigns, and impersonation scams, which blur the lines of what is real and artificial.
2. Cloud Security is Now the Focus
62% of cyber detections are now happening in the cloud and this has made cloud security the focus. With the availability of efficiency in cloud platforms, many Indian businesses are migrating. Misconfigurations of cloud resources and improper use of insecure APIs have become harassment involved threats for organizations to contend with. Securing cloud environments can be just as daunting as securing traditional information technology infrastructure.
3. Ransomware-as-a-Service and Supply Chain Attacks
Ransomware still tops the threat list of any security professional. However, delivery methods have evolved also, this has been heightened with Ransomware-as-a-Service (RaaS) platforms allowing less talented threat actors to launch sophisticated attacks to patients, providers, government and financial institutions. We have also seen an increase in attacks on software supply chains, as well as attacks on critical infrastructure, also as a result greed, targeting threat actors tend to consider less secure partners than large organizations.
4. An emphasis on Healthcare, Banking, and Hospitality
Healthcare has been the leading targeted sector in 2024-2025 (accounting for 21.82% for all attacks) on account of its crucial nature and the worth of personal and financial data. Hospitality (19.2% collectively) and banking (7.2% collectively) have also received significant attack frequencies, as these sectors are also of particular interest for extortion, breaches, and ransomware.
5. Challenges of 5G, IoT, and Quantum Computing
With India rolling out its 5G networks, and the increasing explosion of IoT devices in society, the attack surface has been expanded. More endpoints lead to a greater chance for attackers to leverage opportunity. Finally, quantum computing is advancing rapidly to the point that organizations will soon need to implement quantum-resistant encryption.
6. Behavior-based threat detection
In India, the shift in cyber defense from signature-based approaches to behavior-based analytics means that analytics is now representing 14.5% of detections, an increase from 12.5% last year. The behavior of adaptive threats, novel, malware using adaptive techniques, are less likely to be detectable using more traditional detection.